Explain the current status, problems and suggestions of SM series algorithm financial IC card application
In order to better adapt to the multi-application needs of financial IC cards across industries, compatible with the latest international standards, and promote the integration of financial lC cards and network payment and mobile payment, the People's Bank of China promotes the rapid development of the promotion and application of financial IC cards, simultaneously Added and revised the "China Financial Integrated Circuit (IC) Card Specification" (PBOC2.0), and officially released JR/T 0025-2013 "China Financial Integrated Circuit (IC) Card Specification on February 5, 2013 ( V3.0)" (PBOC3.0). PBOC3.0 defines the application of SM2 (asymmetric algorithm), SM3 (heavy algorithm) and SM4 (symmetric algorithm) developed by China in the field of financial IC card security.
I. Overview of SM series algorithms and applications
The SM series algorithm refers to the commercial cryptographic algorithms and specifications independently developed by China by the National Cryptographic Bureau. In the field of financial IC cards, SM2, SM3, and SM4 in the SM series algorithm correspond to RSA, SHA-1, and 3DES in the international common cryptographic algorithm, respectively.
At the beginning of 2012, the People's Bank of China and China UnionPay jointly established the “GUOM J Algorithm†in the field of financial IC card application technology research group to discuss the application of SM series algorithm in the financial field, together with domestic chips, systems, POS, encryption machines and other manufacturers. The SM series algorithm implementation and transaction tool transformation have been fully demonstrated. The application of SM series algorithm in the field of financial IC card is firstly the application of domestic chip, followed by the application of SM algorithm in key products and related systems such as domestic chip, POS machine and encryption machine. At present, many domestic chip manufacturers have passed the safety certification of the bank card testing center, and the key products supporting the SM series algorithm have been or are being certified by relevant departments.
Second, the status of financial IC card and SM series algorithm application
1. Jinluo IC card promotion and application has achieved remarkable results, and the importance of safety has become increasingly prominent.
Since the launch of the financial IC card in Hunan Province in 2009, after nearly four years of practice and development, it has achieved remarkable results in card issuance, environmental transformation, and industrial application. As of May 2013, Hunan Province has issued more than 6.8 million cards (not financial social security cards), with an average monthly increase of more than 600,000. The financial IC card acceptance environment has been completed. This year, 28 non-contact providers will be built in the province. ring. In terms of public sector applications, 21 public transport applications have been signed, covering 12 cities and prefectures across the province. The financial lC card has penetrated into the public service areas of Hunan Province, such as social security, medical care, and public transportation, which are related to the national economy and the people's livelihood. The social influence is increasing, and its safety importance is increasingly prominent.
2. Financial information security requirements continue to improve, SM series algorithms are included in the specification
In 2009, after the MIFARE CLASSIC IC card cryptography algorithm was cracked, the related industry chain links have started the SM series algorithm transformation work. At present, the products supporting the SM series algorithm have been widely used in government, military, colleges, central enterprises, state-owned enterprises and other high security level units. use.
In 2012, in order to improve the information security level in the financial sector, the General Office of the National Development and Reform Commission issued the Notice of the National Development and Reform Commission Office on Organizing and Implementing the 2012 Special Issues Concerning the Safety IC Card and Password Application in the Financial Sector, and decided to launch the 2012 Financial Sector. The work of “safety IC card and password application special†is given to the industrialization of security IC card and password key products in the financial field, the detection of key products in the financial field, the revision of relevant security standards in the financial field, and the application of security IC card and password application in the financial field. Special fund support. At the beginning of 2013, the newly promulgated PBOC 3.0 specification incorporated the SM series of algorithms, indicating that the SM series of algorithms will be applied in the financial field.
Third, SM series algorithm application transformation needs
At this stage, the financial IC cards issued by China's banking industry all use foreign chips and international common standard algorithms (except for financial social security cards). The promotion and application of SM series algorithms requires a long time and complicated process to ensure that their promotion risks are controllable and The financial IC card promotion is better coordinated, and the SM series algorithm is promoted and applied in a “step-by-step, step-by-step replacement†manner. That is to say, in the future period, China's financial IC card is compatible with international common standard algorithms and SM series algorithms, and adopts compatible methods for the transformation of various links in the industrial chain. After all the conditions are mature, it will be gradually replaced to avoid the card environment and banks for residents. The business has an adverse impact. According to the requirements of PBOC3.0 for the SM series algorithm, the Changsha Zhongzhi Branch of the People's Bank of China has conducted research and summary on the transformation needs of various links in the industrial chain through the preliminary investigation. The situation is as follows.
1.CA transformation
At present, China's authoritative CA center is the China Financial Certification Center (CFCA). Referring to the current root CA specification, the transformation of the SM system involving the SM series algorithm mainly includes generating the root CA key, the root CA public key certificate, the issuing bank certificate, and the administrator certificate by using the SM2 algorithm, including certificate signature and encryption in the application. And check and decrypt, and so on.
2 financial IC card upgrade
As an important part of the SM series algorithm transformation, financial IC cards need the support of chip and card operating system (COS). After the transformation, there are two types of card products: international, SM series dual algorithm and single SM series algorithm. According to the research, at present, many domestic mainstream chip manufacturers have the ability to mass-produce dual-algorithm chips. The relevant card vendors have completed the development of COS transplantation and have applied for inspection by relevant departments.
3. Payment system transformation
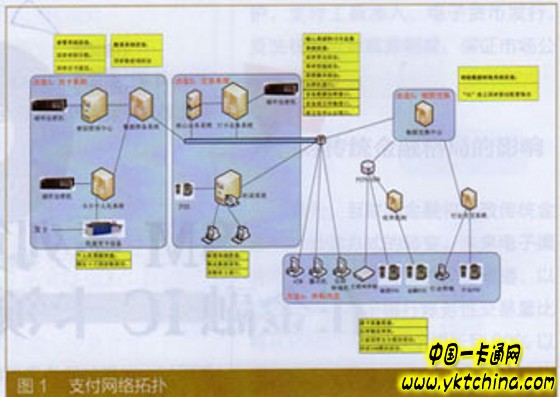
Financial IC card payment applications are mainly composed of card issuing systems, trading systems, UnionPay switching centers, and industry application platforms (Figure 1). Among them, closely related to the transformation of the SM series algorithm are the two systems of issuing and trading. The key transformations of each backbone system and its subsystems are as follows.
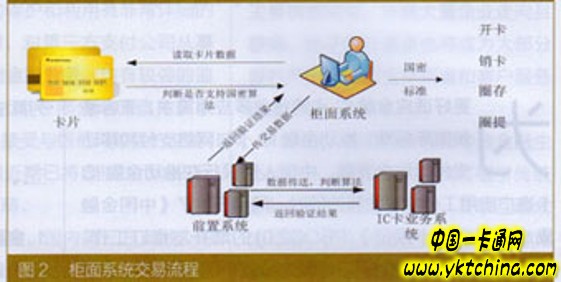
(1) Counter surface process: As shown in Figure 2, compared with the original cabinet system business process, after the SM series algorithm is compatible, the main transformation point is: the card reader module increases the reading of the card data (password algorithm), The counter covers the transaction message interface for secure authentication. Before the service processing, the card reader determines whether the card supports the SM series algorithm through interaction, and supports the SM series algorithm for subsequent business operations, and calls the international common standard algorithm if it does not support.
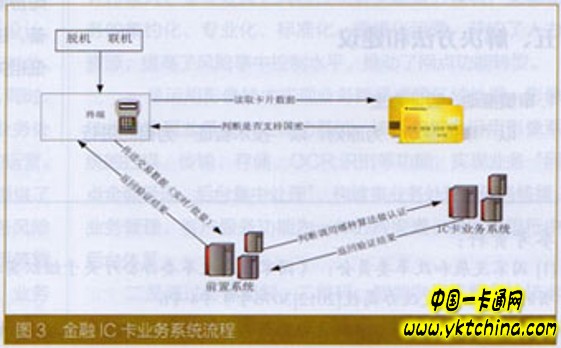
(2) Transaction process: As shown in Figure 3, the transaction process transformation mainly involves the card product management module, template management module, security authentication interface, 55 domain resolution module and transaction interface involving security verification in the IC business system, involving security. Service interface transformation. In the case of dual-algorithm IC card transactions, the terminal SM algorithm is supported to support the indicator and the DDA/SIDA authentication of the SM algorithm. After the transaction process is modified, in the transaction process, the IC card service system needs to determine the SM series algorithm interface or the international common cryptographic algorithm interface in the key management system according to the algorithm identifier in the application data of the card issuing industry, and perform legality authentication and MAC. Calculation.
(3) Core system: It is divided into two ways: the IC card business system and the core system are merged and separated. The former needs to add a secure authentication interface that supports the SM series of algorithms, while the latter remains intact.
Cixi Dujia Electronic Appliance Co., Ltd. , https://www.cixidujia.com